- What is PAN tokenization?
- What is network tokenization?
- How does network tokenization work?
- What challenges does network tokenization address?
- Benefits of network tokenization
- What types of businesses need network tokens?
- How to implement network tokenization?
- Akurateco’s approach to network tokenization
- FAQ
With the rapid growth of e-commerce, merchants and payment service providers are constantly looking for ways to boost payment success rates. One of the most effective strategies to achieve this is through network tokenization.Below we will explain in more detail what network tokenization is, what benefits token provision can bring to merchants, as well as examine how network tokenization for merchants works on the Akurateco example.
What is PAN tokenization?
Before we talk about network tokenization, let’s look at PAN (Primary Account Number) tokenization. This technology, also known as just tokenization, has been used by banks and payment providers for many years.
Tokenization is the process of replacing a customer’s bank card number (PAN) with a token – a randomly generated character set that is used to process payments so as not to reveal the customer’s actual card number. For example, card number 1234-5678-9101-1121 will be turned into a randomly generated token such as 8B6H45L2T5D521R1.
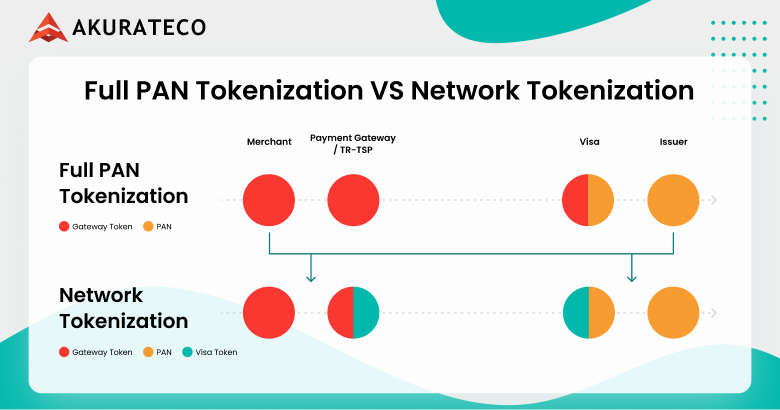
There are several parties involved in the tokenization process, including the customer, merchant, payment provider, card network, and issuing bank. In PAN tokenization, the token was created on the payment provider side and transferred to the merchant for storage. Thus, if attackers accessed the token on the merchant or payment provider’s website, the risk of leaking and using the real card data was lower, but not minimized, because the token could be decrypted into the real card number.
Although PAN tokenization is now widely used to secure online payments and card data storage in payment systems, the growing complexity of threats requires new solutions — this is where network tokenization explained makes all the difference.
What is network tokenization?
Unlike traditional PAN tokenization, which stores the token on the merchant and payment provider side, with network tokenization, the token is generated and stored on the international payment system side (e.g. Visa, Mastercard). A network token is harder to hack, so network tokenization provides a uniform level of protection at all payment stages.
According to research conducted by Visa, network tokenization reduces payment fraud by an average of 26%. At the same time, nothing changes for the customer. His payment happens in a second without any extra hassle. In addition, network tokenization increases customer authorization rates by 3% higher than traditional tokenization, resulting in higher profits for businesses.
Network tokenization also works on the basis of integration with the payment network ecosystem, so tokens can be dynamically updated as needed. For example, if a customer’s bank card expires and they exchange it for a new one, the updated card number will automatically be assigned to the same token. Thus, network tokenization makes payments even more convenient for customers, as they will not need to update their card data after the expiration date of the previous card.
How does network tokenization work?
The basic algorithm of network tokenization includes the following steps:
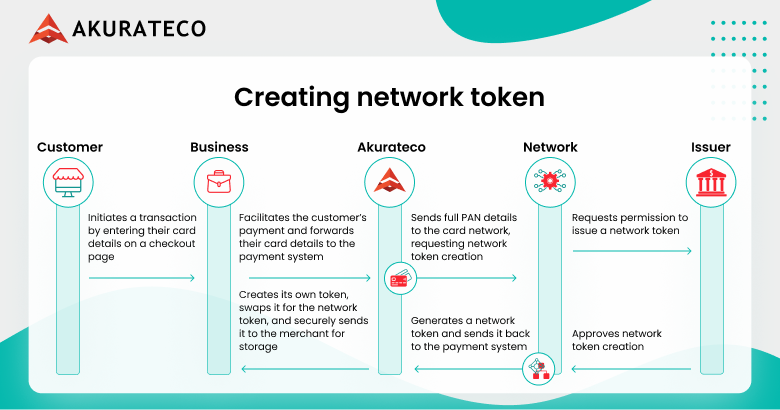
- The customer enters their card details on a merchant’s checkout page.
- A payment system sends full PAN details to the card network, requesting network token creation.
- The card network contacts the issuing bank for approval, generates a network token, and returns it to the payment system.
- The payment system creates its own token, swaps it for the network token, and securely sends it to the merchant for storage.
Network tokenization technology truly comes into the spotlight when the customer returns to the checkout page.
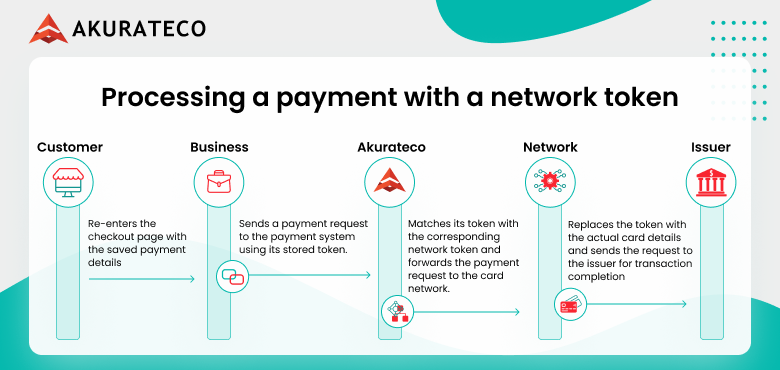
- When the customer re-enters the checkout page, their payment details are securely prefilled.
- After the customer initiates the payment, the merchant sends a payment request to the payment system using its stored token.
- The payment system matches it with the network token and forwards the request to the card network, which replaces the token with actual card details before sending it to the issuer for transaction completion.
What challenges does network tokenization address?
Network tokenization addresses several challenges related to data security and compliance. Below, we are
Data breaches
By replacing sensitive data with tokens, network tokenization decreases the risk of data breaches and the potential consequences, such as financial loss, reputational damage, and legal liabilities.
Data privacy rules
Network tokenization aids businesses deal with data privacy rules like the General Data Protection Regulation (GDPR) and the PCI compliance tokenization by lessening the storage and processing of sensitive information.
Data stealing
Network tokenization makes it difficult for unauthorized individuals to get and steal sensitive information, even if they were to intercept network traffic.
Data compliance
Network tokenization can help organizations demonstrate compliance with data privacy regulations by reducing the amount of sensitive information they handle.
Data theft
By preventing the theft of confidential data, network tokenization helps to safeguard individuals and businesses from identity stealing, financial fraud, and other consequences.
Benefits of network tokenization
Tokenized transactions using network tokens provide many benefits to merchants and their customers. Let’s explore the advantages by analyzing Cybersource (a network tokenization provider) and Akurateco (a payment solution provider) as an example.
Fraud reduction
If you need to perform an acquiring transaction (e.g., purchase), one network token is not enough. In this scenario, it is accompanied by another dynamic value – the network token cryptogram, which is valid for 15 minutes. This advanced method of protection changes with each request Akurateco receives from Cybersource.
Up-to-date data
Since the schemes maintain the end-to-end tokenization process, network tokens are always up-to-date, even if the card details expire. For example, if your card is reissued and your PAN is changed, your network token will remain the same.
The bank issuer informs Visa of the changes. Accordingly, Cybersource sends this information to Akurateco so you don’t have to enter your card details, PAN number, and bank identification number (BIN) number again.
Uninterrupted user experience
Since Akurateco works through Cybersource and partners with Visa, all your credentials are stored here, which you can easily transfer. This means organizations and merchants have their separate login and vault in Cybersource, where their tokens are kept.
What types of businesses need network tokens?
Every business that sells online can benefit from card networks for the reasons listed in the previous section. However, there is a special utility for those businesses that offer subscription services.
These are based on recurring payments, but if the customer’s card expires, the payment will not be honored, resulting in a lapse or loss of revenue. Because network tokens dynamically update the latest details, these businesses are less likely to experience failed payments and decline customer churn.
How to implement network tokenization?
Implementing network tokenization involves several key steps:
- Assessment: Businesses should conduct a thorough evaluation of their existing data security infrastructure and identify the sensitive information that needs to be protected.
- Selection of a tokenization solution: Choose a tokenization solution that meets the organization’s specific needs, including security requirements, compliance standards, and scalability.
- Integration: Integrate the tokenization solution with existing systems and applications. This may involve modifying existing code or developing new interfaces.
- Data migration: Migrate sensitive data to the tokenization system. This process may require careful planning and coordination to ensure that information is not compromised during transaction processing.
- Testing and validation: Thoroughly test the tokenization solution to ensure that it is working as expected and that sensitive information is being protected effectively.
- Ongoing management: Continuously monitor and manage the tokenization system to ensure its security and effectiveness. This includes regular updates, security patches, and compliance audits.
Companies should look for support for network tokenization in their selected payment providers to ensure a seamless and secure experience.
Akurateco’s approach to network tokenization
Akurateco stands out as a white-label payment software provider that offers a range of custom products and services for businesses of all sizes. With a strong focus on security and reliability, Akurateco provides clients with a comprehensive suite of solutions, including network tokenization.
With a commitment to protecting sensitive data and ensuring compliance with industry regulations, our approach is aimed at minimizing the transfer of card data from the customers, merchant Application Programming Interface (API), and acquisition to Akurateco. The joint product of Visa, Mastercard, and American Express is made in international payment systems with the aim of increasing security in card data exchange. Akurateco is one of the first companies to work through Visa and Mastercard to assign a unique token instead of real card data for better security.
With such advanced security measures as PCI DSS Level 1 certification and regulatory adherence including GDPR, HIPAA, and PSD2, Akurateco ensures you can securely handle and transmit cardholder data. Start streamlining your payment processes today and forget about high operational costs and risks!
Excited to leverage advanced network tokenization on a cutting-edge network tokenization platform?
FAQ
What are network tokens?
Network tokens are a type of digital identifier used to securely represent a cardholder’s payment information in online transactions. They replace the actual card number (also known as the Primary Account Number or PAN) and card expiration date with unique network tokens that can be used in place of the number.
How can network tokenization benefit businesses?
Network tokenization improves business security by reducing fraud risk and saving from data breaches. It also enhances operational efficiency by simplifying PCI DSS compliance, decreasing payment failures, and other fraud-related costs.
What kind of businesses need network tokenization?
Network tokenization is useful for businesses that manage a large volume of online or digital payments, store customer payment information, or have a high risk of fraud. These feature e-commerce platforms, subscription services, financial institutions and fintechs, healthcare providers, hotels, airlines, travel booking sites, retailers with multi-channel sales, marketplaces and payment processors, gaming and entertainment, nonprofits, and donation platforms.
How to implement network tokens for my business?
Integrate tokenization into your payment system, replace card numbers with tokens, and test before launching. Update workflows to use tokens, and work with your provider to tokenize stored information. Communicate the change to customers, emphasizing security improvements. After launch, monitor performance, maintain compliance, and train your team on the new system.