
- PCI DSS Compliance
- What is PCI DSS v4.0?
- Overview of Changes in PCI DSS 4.0
- Factors to Consider in Choosing Between Customized and Directed Approaches
- Timeline for Implementing PCI DSS v4.0
- Navigating the Transition to PCI DSS v4.0
- PCI DSS Requirements
- Revisions in PCI Documentation
- Introducing Akurateco’s PCI DSS-Compliant White-Label Payment Software
- Conclusion
Undoubtedly, the rapid evolution of fintech expands our capabilities in the online payment sector. Yet, it also presents new challenges when it comes to fraud. With evolving security practices to combat changing threats, the Payment Card Industry Data Security Standards (PCI DSS) are undergoing the latest version update, PCI DSS 4.0.
In this article, we’ll provide a comprehensive guide to PCI DSS v4.0, delve into its requirements, present an overview of the primary changes compared to v3.2.1, and navigate a seamless transition to version 4.0.
PCI DSS Compliance
Payment Card Industry Data Security Standards (PCI DSS) is the global set of security standards designed to protect credit card data during online transactions. Compliance with PCI DSS is required for any business or organization that processes, stores or transmits credit card information.
What is PCI DSS v4.0?
The PCI Security Standards Council releases a new version of the Payment Card Industry Data Security Standards every two years. It is necessary to keep up with emerging security threats and technological advancements while maintaining standard effectiveness. PCI DSS 4.0 is the latest major version of the Payment Card Industry Data Security Standards with quite a lot of changes. This is why the version number is changed from v3.2.1 to 4.0, indicating serious changes in requirements and controls.
PCI DSS version 4.0 was officially released in March 2022 and is currently in force. The previous version, PCI DSS v3.2.1, will remain active until March 31, 2024. This will allow organizations a transition period to implement the latest standard.
Overview of Changes in PCI DSS 4.0
PCI DSS v4.0 has been updated with several changes aimed at achieving four main objectives:
Guarantee that PCI standard aligns with the evolving security requirements of the payment industry
PCI DSS 4.0 changes include detailed requirements for scoping validation. They also have enhancements to cardholder data transmission protection, anti-phishing and social engineering, and expanded requirements for risk assessment management, authentication, and cloud considerations.
Emphasize security as an ongoing and continuous process
The PCI Security Standards Council underscores the importance of making secure credit card payments a daily priority. It emphasizes the organization’s ongoing commitment to security beyond passing an assessment.
Improve validation methods and procedures
In alignment with the new PCI DSS 4.0, validation methods and procedures, including the PCI DSS Self-Assessment Questionnaire (SAQ) and Attestation of Compliance (AoC), have undergone evaluation and improvement and were officially released in April 2022.
Introduce flexibility and support for additional methodologies to achieve enhanced security.
Version 4.0 brings forth the idea that many companies provide security solutions that align with the intent of a PCI DSS security objective. However, they might not fulfill a specific requirement. To address this, PCI DSS v4.0 introduces the concept of validating a security control through a Customized Approach. Past validation methodologies will be referred to as a Directed Approach.
Factors to Consider in Choosing Between Customized and Directed Approaches
To determine whether a Customized or Directed Approach is right for your organization, you should first understand their fundamentals.
The Directed Approach has been used by entities and assessors to implement PCI DSS requirements for years. It is a good fit for organizations with controls implemented for meeting PCI DSS requirements that are comfortable with them. It’s equally suitable for organizations new to PCI DSS and seeking specific guidance on meeting security objectives.
In contrast, the Customized Approach offers enhanced flexibility for organizations looking for alternate security controls or new technologies aligned with the PCI DSS Customized Approach Objective. While it may appear to be an easier path to PCI DSS certification, it demands a more substantial initial effort from the organization. A lot of effort is put into ensuring proper implementation, supported by necessary documentation and effective assessment.
To qualify for the Customized Approach, organizations must meet specific requirements. For instance, it’s only applicable to organizations undergoing Qualified Security Assessor (QSA) / Internal Security Assessor (ISA) audits and not available for those opting for self-assessments via Self-Assessment Questionnaires (SAQs).
To learn more about the requirements and elements of the Customized Approach, check out PCI DSS v4.0 Requirement 12.3.2 and Appendices D and E on the official website.
Timeline for Implementing PCI DSS v4.0
The timeline for implementing PCI DSS 4.0 involves several crucial dates:
March 2022 – PCI DSS version 4.0 is officially released
In March 2022, PCI DSS v4.0 was officially released and went into effect. As for PCI DSS v3.2.1, it will stay in effect for two years following the publication of v4.0. During this period, organizations are given the time to familiarize themselves with the changes in v4.0. They can also update reporting forms and templates, as well as plan and implement the necessary changes to meet the v4.0 requirements.
March 31, 2024 – PCI DSS version 3.2.1. is retired
Until March 31, 2024, organizations have the option to undergo assessments using either PCI DSS v3.2.1 or v4.0. Starting March 31, 2024, v3.2.1 will be retired, and v4.0 will be the sole version available for certification. However, if your company has obtained v3.2.1 certification just before March 31, 2024, you have another year since your previous certification before you’ll need to update it to v4.0.
To understand when to begin the migration process to v4.0, you need to consider your company’s current assessment cycle (if you are already PCI DSS certified). For instance, if your annual assessment occurs in January, the migration to PCI DSS version 4.0 should be finalized by January 2025. But, if your organization undergoes a yearly assessment in May, the migration to v4.0 should be completed by May 2024.
March 31, 2025 – new PCI DSS 4.0 requirements become effective
On March 31, 2025, PCI DSS version 4.0 becomes a single certification standard. Furthermore, on this date new PCI DSS 4.0 requirements become effective. Organizations are given until March 31, 2025, to gradually implement new requirements initially identified as best practices in v4.0. Before this date, organizations are not required to validate these requirements.
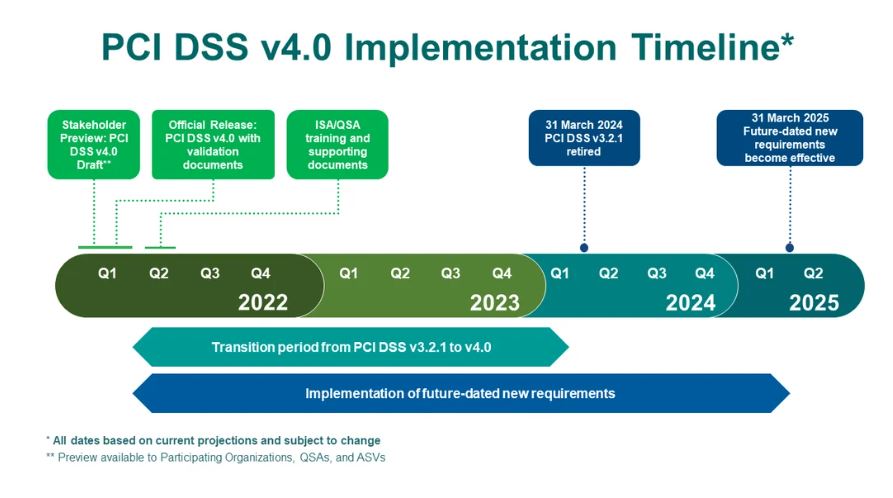
Source: Countdown to PCI DSS v4.0
Navigating the Transition to PCI DSS v4.0
With PCI DSS 4.0 approaching fast, it’s time to start the transition process from v3.2.1 as early as possible. To transition to PCI DSS v4.0 on their own, organizations should conduct an assessment of the technological landscape. This will enable them to identify and address any gaps in compliance with the updated PCI DSS version. They include:
- Updating and patching systems, including OS and applications.
- Implementing new security controls.
- Adjusting encryption protocols, access controls, and network configurations.
- Providing technology training for staff.
- Enhancing logging and monitoring systems for audit purposes.
- Updating or acquiring security assessment tools.
- Improving incident response and detection capabilities.
Maintaining PCI DSS compliance independently and constantly ensuring its alignment with the latest requirements is a challenging and time-consuming process. Luckily, there is a hassle-free alternative – a pre-built, PCI DSS-certified payment system.
PCI DSS Requirements
Twelve core PCI DSS requirements are designed to protect cardholder data and safeguard organizations against potential breaches. PCI DSS core guidelines remain consistent across all versions but incorporate updates introduced with each new release. Therefore, PCI DSS 4.0 requirements contain changes and updates introduced with the new version. Let’s break them down:
Installing and Maintaining a Firewall
The first step towards achieving PCI DSS 4.0 compliance is to use a firewall to control and secure data flow between internal and external networks. PCI DSS specifies how to configure your firewall and routers properly to ensure that the firewall acts as an effective security guard, allowing only authorized and secure data to pass through.
Eliminating Vendor-Supplied Defaults
As it is easy as a pie for a cybercriminal to cycle through common default passwords, organizations are required to change vendor-supplied defaults and settings on systems and devices to reduce the risk of unauthorized access. This applies to critical infrastructure like routers, servers, and any technology handling sensitive information.
Furthermore, it’s not just about changing passwords for system-level access. It’s also crucial to avoid default passwords for user accounts, so ensure your users are not allowed to use defaults.
Safeguarding Stored Cardholder Data
Credit card numbers and other sensitive data are prime targets for fraudsters. Therefore, businesses must encrypt it in a secure, unreadable format, adding a layer of protection against potential breaches.
PCI DSS 4.0 mandates businesses to incorporate encryption measures for credit card numbers and other sensitive data during storage. It is done by keeping it in secure environments, such as encrypted databases. In this way, even if unauthorized parties gain access to the data, they won’t be able to understand or misuse it.
Encrypting Cardholder Data Transmission
Organizations must also safeguard credit card information through encryption as it travels over the internet and other public networks. This is because it is more vulnerable to cybercriminal attacks when transmitted. To protect sensitive data, businesses must use secure communication channels, such as HyperText Transfer Protocol Secure (HTTPS), to encrypt data in transit.
An enhancement introduced in PCI DSS v4.0 involves specific guidance on implementing multi-factor authentication (MFA).
Leveraging and Updating Anti-Virus Software
Installing and regularly updating anti-virus software is vital to protecting your systems from malicious software (malware). It is also necessary to perform automated updates and regular scans of all systems to identify and eliminate any potential malware threats. Also, it’s critical to apply anti-virus software across various systems vulnerable to malware attacks, such as servers, workstations, employee computers, laptops, tablets, remote devices, and on-site devices.
Developing and Maintaining Secure Systems and Applications
As you cannot protect your system with anti-virus alone, the sixth PCI requirement emphasizes the importance of consistently updating and securing software. This entails implementing a procedure for regularly updating software and applications, encompassing operating systems, server software, and any third-party applications used in the organization. The aim is to protect your system from emerging threats and vulnerabilities.
Restricting Access to Cardholder Data
Cardholder data is sensitive information extremely vulnerable to the risk of unauthorized use or disclosure. Hence, PCI DSS 4.0 requirements mandate organizations to provide access to cardholder data on a need-to-know basis. This entails defining roles and responsibilities within the organization and providing access to cardholder data exclusively to employees who require it for their specific job responsibilities. By default, employee access to the cardholder data environment (CDE) should be restricted.
Authenticating Access to Components of the System
Implementing robust authentication methods is crucial for controlling access to system components. Therefore, each employee must possess an exclusive username and password for system access. In this way, you can trace suspicious activity back to a specific user in the event of a data breach or unauthorized access. Furthermore, to comply with this requirement, businesses must enforce robust password policies and implement multi-factor authentication (MFA).
Also, there are several PCI DSS 4.0 changes for organizations to note. In particular, version 4.0 raised the threshold for invalid authentication attempts, increasing it from 6 to 10 before locking out a user ID. Also, it allows access to resources to be determined automatically by dynamically analyzing the security posture of accounts. In contrast, previous versions necessitated password changes at least once every 90 days.
Restricting Physical Access to Cardholder Data
For businesses, securing physical access to cardholder data is as crucial as safeguarding digital access since it could lead to theft, manipulation, or tampering with hardware components. Therefore, organizations must protect physical access to servers, systems, paper files, and workstations that store or transmit sensitive data to prevent fraudsters from tampering with them. To secure them, businesses need to place them in secure data center environments and implement access controls, surveillance, and monitoring systems.
In addition, PCI DSS v4.0 mandates that organizations limit access to consoles in sensitive areas by implementing locking mechanisms when not in use.
Tracking and Monitoring Network Resources and Cardholder Data Access
Monitoring and tracking access to network resources and cardholder data is vital for businesses. It allows them to identify any unauthorized access or unusual patterns that may indicate a potential security threat. To meet this requirement, companies must establish robust logging mechanisms capturing details of every access, including user identity, timestamp, and access to resources. Also, in accordance with PCI DSS requirements, audit trail data should be retained for a minimum of one year, with at least three months of data readily accessible for review.
Testing the security of systems and networks regularly
Regular testing of security systems and processes is crucial for identifying potential vulnerabilities and weaknesses. Organizations can take corrective actions, strengthen their defenses, and mitigate security breaches by identifying vulnerabilities through testing.
PCI DSS requires organizations to conduct penetration testing at least annually, with follow-up remediation and retesting after the report is issued. Quarterly internal and external vulnerability scanning is also mandated, with external scanning requiring an Approved Scanning Vendor (ASV) authorized by the PCI SSC. In addition to these requirements, businesses are highly recommended to perform security audits and incident response testing.
Maintaining a Policy that Enforces Information Security for Employees and Contractors
Last but not least, having a comprehensive information security policy is crucial for creating a secure environment. It should encompass a set of guidelines and rules that articulate the organization’s approach to information security. Note that it should be reviewed every year. along with all other policies and procedures. Also, to educate employees about security policy and enforce it in your workplace, provide training sessions.
PCI DSS version 4.0 introduces several new requirements. Firstly, it requires a formal acknowledgment from personnel regarding their responsibilities. Additionally, entities employing a Customized Approach are now required to conduct a targeted risk analysis for each PCI DSS requirement addressed through the customized approach. Another novel requirement involves documenting and confirming the PCI DSS scope at least once every 12 months and whenever there is a significant change in the in-scope environment. Lastly, PCI DSS v4.0 emphasizes that information about PCI DSS requirements, managed jointly by the Third-Party Service Provider (TPSP) and the entity, should encompass any requirements shared between them.
Revisions in PCI Documentation
The PCI Security Standards Council has released supporting documentation for version 4.0 and PCI DSS 4.0 summary of changes, available for download on the official website via the link below:
These revisions also encompass updates to the supporting Self-Assessment Questionnaires (SAQs). It’s crucial to verify that you are utilizing the appropriate SAQ based on your assessment cycle timing.
Introducing Akurateco’s PCI DSS-Compliant White-Label Payment Software
A renowned global Fintech solution provider, Akurateco, offers a PCI DSS-certified white-label payment system to fintech solution providers and merchants worldwide. This ready-to-use software incorporates cutting-edge payment technologies, boasting over 330 integrations and the option for rebranding the system under your brand identity.
With our solution, Akurateco is in charge of obtaining and renewing PCI certification for our platform. The platform also supports businesses in achieving PCI DSS compliance at Levels 3 and 4 for merchants and Level 2 for PSPs. As Akurateco collaborates with leading Qualified Security Assessors (QSAs), our experts can guide you throughout the compliance process step by step, from preparing documents to achieving PCI DSS certification. We’ll also provide the documentation needed for certification from our side, including details about our system’s architecture and other necessary documents.
If you want to streamline the complexities of maintaining PCI DSS compliance for your business, check out our PCI DSS-certified payment system.
Conclusion
In conclusion, PCI DSS 4.0 introduces critical changes, emphasizing adaptability and enhanced security measures for businesses that handle sensitive credit card data. To simplify the journey towards compliance, consider leveraging Akurateco’s PCI DSS-certified white-label payment system, offering innovative technologies and expert assistance.





